Securing Patient Data and Billing with Zero Trust Architecture in the Healthcare Industry
The Healthcare Industry in US is one of the most vulnerable sectors which faces unprecedented cybersecurity challenges, from ransomware attacks to medical billing fraud. With millions of patient records at risk and compliance demands like HIPAA intensifying, traditional security models are no longer enough. According to the Verizon Data Breach Investigations Report,2024 58% of healthcare cyberattacks target financial and billing data, underscoring the need for Zero Trust Architecture to safeguard revenue cycle workflows. In this blog let us explore how Zero Trust Architecture works, their role in protecting patient data, medical devices, and billing workflows while maintaining regulatory compliance.
Why Healthcare Data is the Prime Target?
Healthcare data has become a prime target for attackers because of the dual values they hold that is the sensitive patient health information along with their payment details. Also, with the rise of telehealth, remote monitoring, and third-party access the traditional security perimeters have become obsolete. The explosion of vulnerable IoMT devices have created vast entry points for attackers.
- The High Value of Patient Data: Patient health records (PHRs) are more valuable because a single stolen medical record can give many information like Social Security numbers, addresses and medical history, that can be used for identity theft and fraudulent claims for years.
- The Erosion of the Traditional Perimeter: The COVID-19 pandemic has accelerated the adoption of telehealth and remote working, which created a new challenge for traditional security tools like VPNs. Clinicians and administrative staff are now accessing sensitive data from their homes, offices, personal devices, and third-party vendor platforms. This has dissolved the old network boundary creating a vast expanded surface for attack.
- The Explosion of Connected Devices (IoMT): Nowadays more internet-connected devices, like infusion pumps, MRI machines, personal monitoring medical devices are used that are difficult to patch or monitor. All these devices are connected on the same network as the EHR, and a single compromised device can become a foothold for an attacker to move laterally across the network and reach high-value systems.
What do you mean by Zero Trust Architecture (ZTA)?
Zero Trust Architecture is a security feature built on the principle of “never trust, always verify.” It protects the electronic health records (EHRs), telehealth platforms, billing systems, and the Internet of Medical Things (IoMT) with continuous monitoring and validation of every user, device, application, and data request each time regardless of their location. This not only reduces risks but also strengthens patient trust and future-proofs healthcare operations by replacing the outdated assumption of trusting everything.
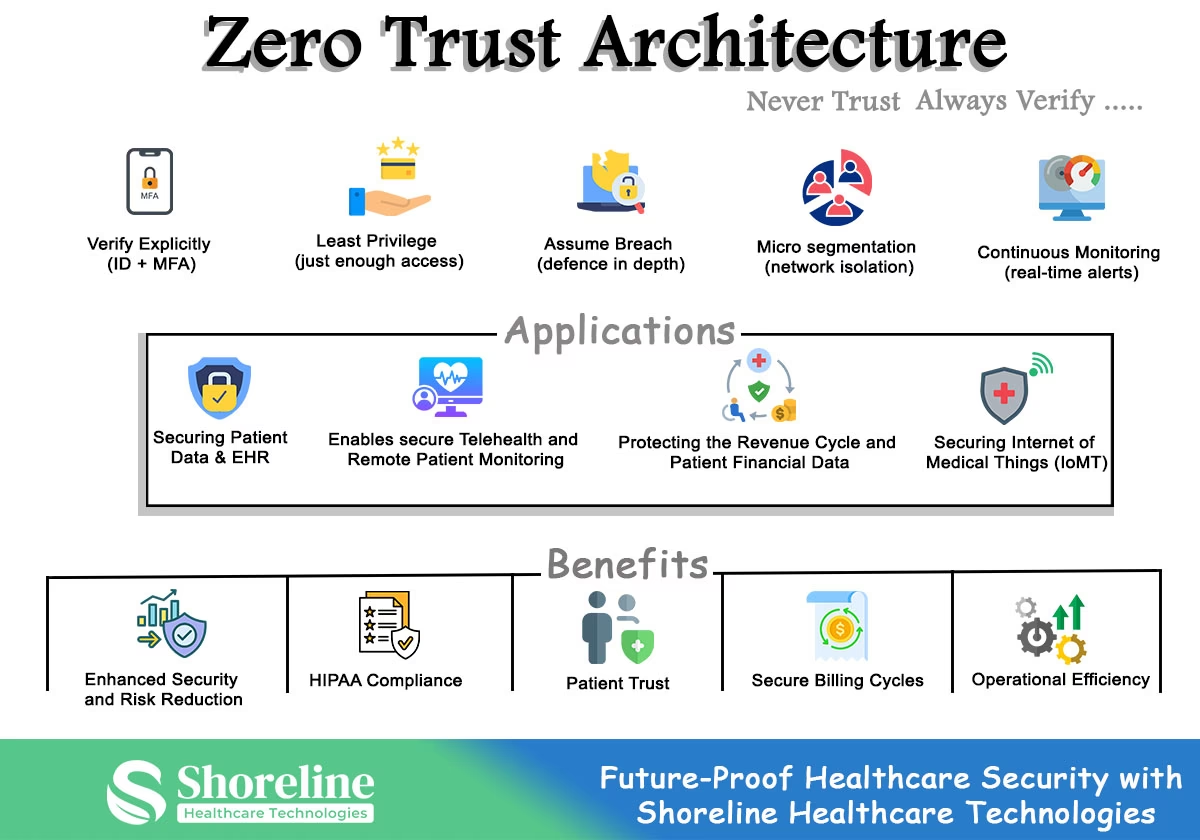
Core principles of ZTA
Verify explicitly Never Trust, Always Verify
This is the central tenet of ZTA and mandates continuous authentication of users, devices, and services. It does not trust any person or entity by default, based on their location inside the network. Every access request is treated as a potential threat and rigorous verification and authorization is done based on all available data points like user identity, device security posture, and the nature of the data requested.
Least Privilege Access
ZTA offers only minimum level of access for all users, devices, and applications necessary to perform their authorized functions. This limited strict permission reduces lateral movement by an attacker and mitigates the risk of insider threats.
Assume Breach
ZTA operates by assuming that an attacker is already present inside the network, and shifts the focus from preventing the perimeter to internal detection and containment. Their goal is to minimize the "blast radius" of any potential breach, and ensures that a compromised account or device cannot be used to move laterally across the network.
Micro-segmentation
ZTA divides the network infrastructure into small, isolated zones with this security method it contains an attack by preventing an attacker who breaches one segment from moving laterally to access other critical systems.
Continuous Verification and Monitoring
ZTA continuously monitors real-time logging, user behaviour and access patterns across the networks to provide security analytics, and anomaly detection.
We at Shoreline Healthcare Technologies have adopted the Zero Trust Architecture (ZTA) across our billing workflows providing a future-proof security model that strengthens trust and efficiency. Our solutions go beyond the traditional perimeter defenses and integrates identity verification, least privilege access, and continuous monitoring to keep both patient data and financial information secure. We align with compliance frameworks like HIPAA and support secure billing cycles. Our continuous growth in the Medical Billing services and innovations can be read at our official press release. Click here to learn more.
Applications of Zero Trust Architecture
Zero Trust in Protecting Electronic Health Records (EHR)
- ✔ Only verified physicians can see patient data with strict access control.
- ✔ Micro segmentation prevents attackers from moving laterally across various systems.
- ✔ Provides encryption both at rest and in transit to secure sensitive PHI.
Zero Trust and Telemedicine Platforms
- ✔ Verifies providers and patient identities with biometric or MFA.
- ✔ APIs that connect telehealth platforms with EHRs and billing systems are secured.
- ✔ Detects anomalies in unusual login times or geographical locations.
Internet of Medical Things (IoMT) and Device Security
- ✔ Device authentication before network connection.
- ✔ Isolates vulnerable IoMT devices from billing systems by micro segmentation.
- ✔ Continuous monitoring to detects compromised device behavior.
Securing Medical Billing and Revenue Cycle Management
- ✔ It provides role-based access controls so that everyone cannot access certain clinical data.
- ✔ Uses AI tools to detect and spot fraudulent billing patterns.
- ✔ Blockchain integration creates tamper-proof billing records.
Benefits of Zero Trust Architecture
Enhanced Security & Risk Reduction
- ZTA reduces both external and internal threats by verifying every access request.
- It protects patient records, billing data, and IoMT devices against ransomware and phishing attacks.
Provides Regulatory Compliance like HIPAA
- Protects ePHI by implementing least privilege, access auditing, and continuous monitoring.
- Simplifies demonstrating compliance during audits.
Protection of Billing Cycles
- Secures revenue cycle systems from fraud and ransomware.
- Reduces downtime in claims processing, reimbursements, and patient billing workflows.
Improves Patient Trust
- Builds a secure platform for telehealth and Remote Patient monitoring services.
- Safeguards sensitive health and financial data thereby improving patient’s trust.
Operational Efficiency
- Automates security checks and access controls.
- Enables physicians and staff to work securely across devices and locations.
Zero Trust Architecture has become an inevitable option in US Healthcare sector. They offer scalable and adaptive framework that helps in addressing ransomware to billing fraud at the same time aligns with all federal and state specific compliances.
Never trust, always verify with Shoreline Healthcare Technologies your trusted partner in transforming healthcare cybersecurity and protecting the revenue cycle from cyber risks.
FAQs
Q1. What role does Zero Trust play in patient trust?
+Zero Trust increases patient trust and organizational reputation by providing high security against cyberattacks and protecting the health and financial data.
Q2. Is Zero Trust mandatory for HIPAA compliance?
+No ZTA is not mandatory for HIPAA compliances, however it helps to the meet HIPAA’s technical standards by safeguarding the patient’s health data.
Q3. What do you mean by IoMT?
+The Internet of Medical Things (IoMT) refers to a network of connected medical devices, software applications, and health systems that communicate via the internet for real-time monitoring and data sharing.
Q4. How can Shoreline Healthcare Technologies support providers with Zero Trust?
+We at Shoreline Healthcare Technologies have implemented ZTA across our revenue cycle operations. Our solutions integrate ID verification, MFA, least privilege access, and real-time monitoring, creating a future-proof security framework for providers.
Q5. Is ShorelineMB the same as Shoreline Healthcare Technologies?
+Yes, ShorelineMB.com is the official website of Shoreline Healthcare Technologies, a leading provider of medical billing and RCM services.



















Contact Shoreline Healthcare Technologies for secure and compliant revenue cycle operations.