Elevating Healthcare Data Protection with Cloud Computing: The Secure Shift
Healthcare organization faces the critical challenge of protecting patient information at the same time allowing the necessary data accessibility for patient care. The traditional on on-site data centers possess significant security risks and are vulnerable to physical threats. And a single malfunction resulting in loss of entire data. This makes the healthcare industry prime target for data breaches, ransomware, and other cyber-attacks. These challenges can be replaced with adopting cloud computing that delivers unparalleled security for healthcare data by replacing the traditional on-site systems with robust, multi-layered defences that helps providers protect sensitive patient information and maintain compliance with regulations like HIPAA. In this blog let us explore the security benefits of cloud-based environment.
Why Security Matters for Healthcare Data?
Healthcare data is highly sensitive and contains detailed information, about patient’s social security numbers, birth dates, addresses, financial data, and medical history. And a single data breach may result in millions of losses to the healthcare organizations, damaging their trust, and disrupting delivery of care. Due to these reasons there arises a need for a strong, secure and reliable platform to maintain the data integrity and stay compliant with state and federal regulations like HIPAA.
What is Cloud Computing and Why is It More Secure?
Cloud computing in healthcare means managing, storing, and processing health-related data over the internet, instead of an in-house server. It is like a professional vault service, with teams of security experts working around the clock to protect sensitive patient information, with high-tech surveillances and multiple layers of protection.
Key Risks in Healthcare Data Protection
Cyberattacks & Ransomware
Hackers target healthcare organizations because of the high value of medical records. Ransomware can lock systems and halt patient care.
Unauthorized Access
Weak passwords or insider threats can expose sensitive patient information.
Data Breaches & Theft
Devices that are lost or stolen with unsecured networks, or phishing attacks may lead to massive breaches of electronic health records (EHRs).
Non-Compliance with Regulatory Frameworks
Non-Compliance with Federal or state regulations may lead to legal penalties, fines, and reputational damage.
Human Error
Mistakes while sending records to the wrong person or misconfiguring cloud storage may also results in unintentional data leaks.
Third-Party Risks
Vendors, contractors, or cloud providers without strong security measures can become weak links in the data protection chain.
System Downtime & Data Loss
Lack of proper backups or disaster recovery planning can result in permanent loss of medical records during outages.
Cloud Computing Delivers Unprecedented Security for Healthcare Data
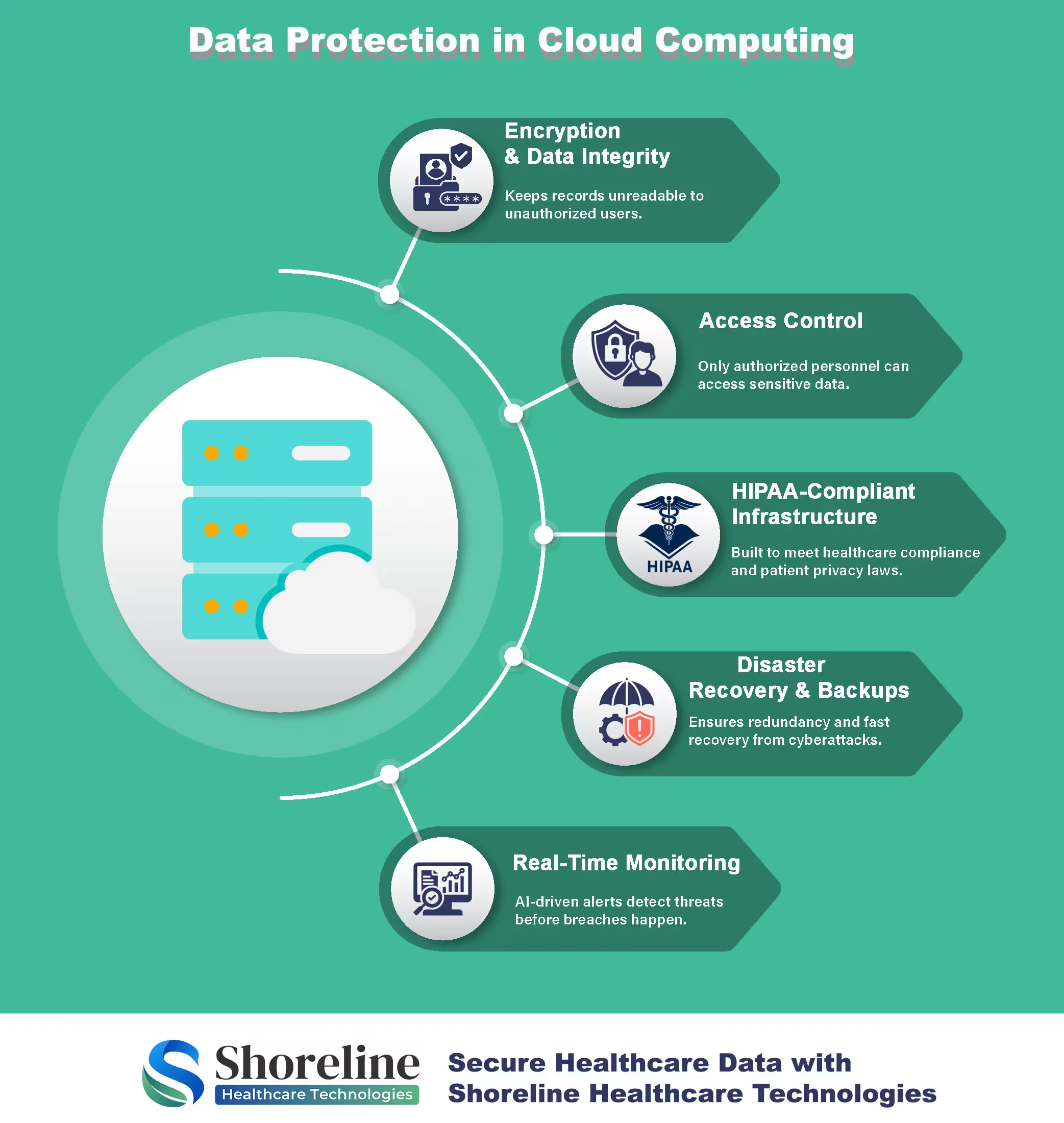
Advanced Encryption
Encryption makes it impossible for unauthorized parties to steal and read the information. Cloud providers use advanced algorithms that scramble the data into codes which are unreadable to anyone without the right key. With "end-to-end encryption," data is protected both ways while it is stored or transmitted.
Strict Access Control
Cloud infrastructure allows fine-tuned controls over who can access the protected data. Their role-based access control (RBAC), make sure that only relevant authorized personnel can access medical records according to their jobs. For example, a front desk assistant, might have access to a patient’s billing information but not their lab results, this ensures data integrity and privacy.
Continuous Monitoring
Cloud systems are monitored 24/7 unlike in-house servers that are checked occasionally. They use advanced artificial intelligence (AI) and machine learning to watch out for unusual activity. They can alert the security team or even shut down the activity automatically on detecting a suspicious login attempt or a large data transfer at an odd hour.
Physical Security
Cloud based data centers are highly secure, located in remote areas and are built to withstand natural disasters. They have biometric scanners, armed guards, and surveillance systems.
Disaster Recovery and Backup
Cloud computing guarantees data redundancy and backups across multiple servers and locations. Hence data remains safe and accessible, even in emergencies. So even if one system fails, another backup is ready to restore operations without disruption. This feature helps to maintain the continuity of the business and makes recovery quicker without affecting the patient care.
Compliance with Regulations
Cloud platform comes with built-in tools for HIPAA compliance and other regulatory standards. They automate logging and audits, tracking every access attempt. This helps healthcare organizations stay compliant without extra hassle.
We at Shoreline Healthcare Technologies offer cloud-based solutions designed with HIPAA-compliant security frameworks and built-in encryption, that provides real-time monitoring and safeguards electronic health records (EHRs) against emerging threats
Benefits of Cloud Computing in Healthcare Security
- Reduces Costs: With the cloud pay as you go model, huge volume of data can be stored without the need for pricey on-site servers.
- Improves Data Accessibility: Providers can access EHRs from anywhere, so that they can speedup care without compromising on security.
- Enhances Data Management: With real-time updates we can keep medical records accurate and secure.
- Scalability: Can accommodates huge volumes of data without any need for additional hardware.
- Data Integrity: Automated backups prevent data loss.
Future Trends in Cloud Security and Healthcare Systems
1. Zero Trust Architecture (ZTA)
Zero Trust Architecture (ZTA) could be the best solution for healthcare data as it works on the principle of “never trust, always verify.” It means every user, device, and transaction must be authenticated every time, reducing the risk of threats. It makes sure that only authorized personnel can access medical records at every step and prevents unauthorized breaches.
2. Blockchain Integration
Blockchain technology is an emerging powerful tool for management of medical records. It creates immutable, distributed ledgers, that promotes data integrity and transparency. Every transaction like accessing, updating, or sharing patient information are time-stamped and securely logged, minimizing fraud and tampering. It acts as an additional layer of protection for healthcare systems.
Cloud computing is revolutionizing the way of handling healthcare data. We at Shoreline Healthcare Technologies provide end-to-end Revenue Cycle Management (RCM) expertise, which means we not only protect your sensitive patient data but also streamline your billing and operational workflows. Outsourcing your billing practices to Shoreline Healthcare Technologies, you gain:
- ✔ Enhanced Security and Multi-layered protection against breaches and ransomware.
- ✔ Full confidence for compliance with HIPAA, CMS, and other state specific regulations.
- ✔ Improve your operational efficiency with secure data systems that integrate seamlessly into clinical and billing processes.
- ✔ Incorporation of AI, cloud-based solutions that are scalable and tailored to fit with your practice
FAQs
Q1. How Cloud Infrastructure Reduces Security Risks?
+Cloud-based platforms implement more advanced firewalls and intrusion detection, and patch vulnerabilities faster by their routine updates, they provide geographically distributed storage, thereby reducing downtime risks.
Q2. Is cloud computing safe for electronic health records (EHRs)?
+Yes. Most of the Cloud platforms are HIPAA-compliant, and a cloud based EHRs are more secure and beneficial with strong data integrity, secure backups, and real-time monitoring.
Q3. What are some common security risks in the cloud?
+Unauthorized access, human error, system misconfigurations, and phishing attacks are some risks of storing the data over the cloud.
Q4. What is Multi-Factor Authentication (MFA)?
+Using two or more factors like PIN, passwords, token code etc to gain access to a system or data is called multifactor authentication.
Q5. Is ShorelineMB the same as Shoreline Healthcare Technologies?
+Yes, ShorelineMB.com is the official website of Shoreline Healthcare Technologies, a leading provider of medical billing and RCM services.
















Contact us today and discover how we help your organization to strengthen its data security while improving operational efficiency.